Why Security Matters
Private keys are the foundation of blockchain ownership. Any WaaS (Wallet-as-a-Service) solution must guarantee secure key management. Particle Network’s security model is built on four principles:- Only the user controls their keys.
- Only the user can initiate signing.
- Accounts must be recoverable across devices.
- No single point of failure should ever exist.
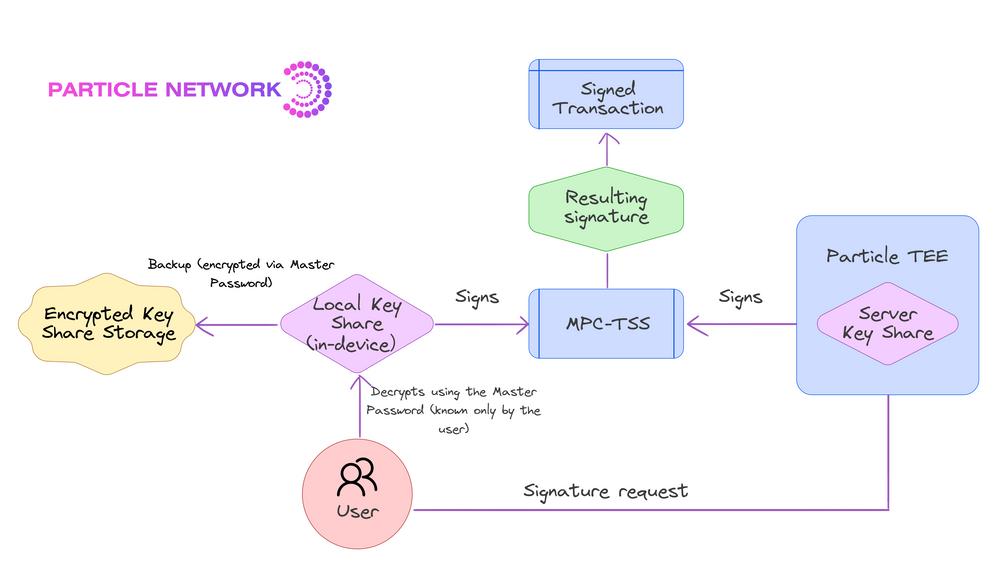
What is MPC-TSS?
Threshold Signature Schemes (TSS) split a secret (the private key) into multiple shares. The full key never exists in one place — even during generation.- A subset of shares (e.g., 2/2 or 3/5) is enough to generate a signature.
- Keys can be refreshed periodically, improving resilience.
- MPC (Multi-Party Computation) ensures computations are done collaboratively without revealing the key.
Particle’s 2/2 MPC-TSS Approach
Particle uses a 2/2 TSS model:- Share 1: stored locally on the user’s device.
- Share 2: stored in Particle’s Trusted Execution Environment (TEE).
- The two shares are never combined, not even during signing.
- Each share reveals nothing about the private key on its own.
- Continuous key refresh makes compromise virtually impossible.
- Extra protection on top of social login.
- Secure cross-device wallet recovery.
Supported Cryptographic Algorithms
Particle implements secure MPC versions of:- 2-Party EdDSA — Solana
- 2-Party ECDSA — EVM chains
Infrastructure Security
Beyond MPC-TSS, Particle’s infrastructure follows strict security standards:- End-to-end TLS encryption
- Segregated public/private networks
- Intrusion detection monitoring
- Hardware Security Modules (HSMs)
- Dedicated Trustee TSS Party-2 Server
